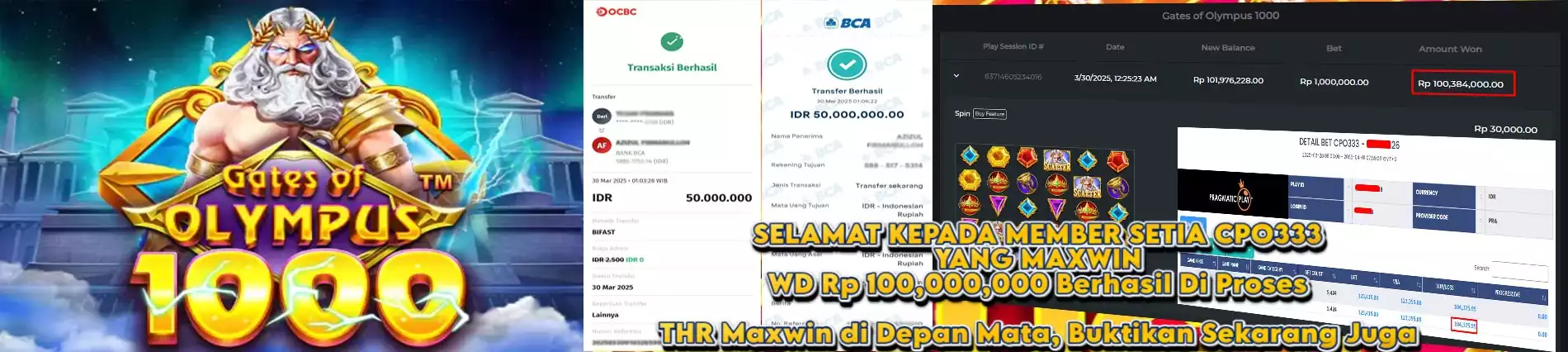
IDR 41,436,426,538
Layanan Customer
Layanan Product

Permainan Terlengkap dalam seluruh platform
Layanan Member
Tambah Dana
Waktu
2
Menit
WITHDRAW
Waktu
3
Menit
Sistem Pembayaran

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE

ONLINE
CPO333 : Platfrom Best Game Online Seindonesia
Home
Home